Commission, October 30, 2019, No M.9538
EUROPEAN COMMISSION
Judgment
BROADCOM / SYMANTEC ENTERPRISE SECURITY BUSINESS
Subject: Case M.9538 – Broadcom / Symantec Enterprise Security Business Commission decision pursuant to Article 6(1)(b) of Council Regulation No 139/20041 and Article 57 of the Agreement on the European Economic Area2
Dear Sir or Madam,
(1) On 26 September 2019, the European Commission received notification of a proposed concentration pursuant to Article 4 of the Merger Regulation by which Broadcom Inc. (“Broadcom” or the “Notifying Party”, United States of America) acquires within the meaning of Article 3(1)(b) of the Merger Regulation sole control of parts of Symantec Corporation (“Symantec”, United States of America) (the “Transaction”). The Transaction only concerns Symantec’s Enterprise Security Business (“SESB” or “Target Business”). Broadcom and Symantec are collectively referred to as the “Parties”.3
1. THE PARTIES
(2) Broadcom, headquartered in San José, California, United States of America, is a technology company that designs, develops, and supplies a broad range of semiconductors as well as infrastructure software solutions that enable customers to plan, develop, automate, manage and secure applications across mobile, cloud, distributed and mainframe platforms.
(3) Symantec, headquartered in Mountain View, California, United States of America, designs, manufactures, and provides security software, storage, and systems management solutions to consumers and enterprises.
(4) SESB offers a mix of products, services, and solutions, unifying cloud and on- premises security elements, to provide enterprises with advanced threat protection and information protection across their endpoints4, networks, email, and cloud applications.
2. THE CONCENTRATION
(5) The Transaction consists of the acquisition of sole control of SESB by Broadcom, on the terms, and subject to the conditions, of an asset purchase agreement (“APA”) entered into between Broadcom and Symantec on 8 August 2019. The acquisition concerns Symantec’s business, operations and activities reported as the “Enterprise Security” segment5, which includes making, marketing, selling and providing the related products and services.6 The APA includes a detailed list of assets, such as employees, products and services, customer contracts, property rights and technologies belonging to SESB. After the Transaction, SESB will be wholly owned by Broadcom.
(6) The Transaction does not include Symantec’s Consumer Cyber Safety business unit, over which Symantec will continue to exercise sole control.
(7) The Transaction therefore constitutes a concentration pursuant to Article 3(1)(b) of the Merger Regulation.
3. UNION DIMENSION
(8) The undertakings concerned have a combined aggregate world-wide turnover of more than EUR 5 000 million (Broadcom: EUR 21 185 million, SESB: EUR 2 006 million).7 Each of them has an EU-wide turnover in excess of EUR 250 million (Broadcom: EUR […], SESB: EUR […]), but they do not achieve more than two- thirds of their aggregate EU-wide turnover within one and the same Member State. The notified operation therefore has a Union dimension pursuant to Article 1(2) of the Merger Regulation.
4. RELEVANT MARKETS
4.1. Introduction
(9) Both Parties are active in the supply of software. The relevant market(s) will be examined in section 4.2. In line with previous decisions8 relating to the software industry, in order to identify the narrowest possible product markets, the Commission relied on market segmentations set by the market intelligence company Gartner Inc. (“Gartner”).9 Gartner is a well-known market intelligence source for software markets and provides very granular sub-segmentations and corresponding market share information.
(10) Broadcom is also active in the supply of a broad range of semiconductor products. As there is no plausible relationship between Broadcom’s activities in the market for the supply of semiconductors (or any potential sub-markets thereof) and SESB’s activities in the market for the supply of software (or any potential sub-markets thereof), the Transaction does not give rise to a significant impact on any other markets.10,11 Therefore, for the purpose of the present decision, the Commission will not discuss further Broadcom’s activities in the market (or any potential sub- markets) for the supply of semiconductors.
4.2. Software supply
(11) The Transaction concerns the market for the supply of software. More specifically, the Parties are both active in the supply of infrastructure software, which refers to a wide category of software products that: (i) provide the infrastructure for applications to run on a server; (ii) can be accessed from a variety of clients over a network; and (iii) are capable of connecting to a variety of information sources.12
(12) Within infrastructure software, the Parties’ activities only overlap in the supply of (i) enterprise security software; and (ii) IT operations management (“ITOM”) software for enterprise use (as illustrated in Table 1 of section 5.1). Therefore, for the purpose of the present decision, the Commission will focus on these two areas within infrastructure software.
(13) Furthermore, the Commission considered whether the Transaction could give rise to a significant impact on any other enterprise software markets in which Broadcom has a market share above 30%, i.e. the potential markets for ITOM mainframe tools and for application development mainframe tools. Therefore, the Commission will also examine these two areas.
4.2.1. Product market definition
(14) The Commission has in the past classified software products on the basis of functionality, the end-user (enterprise software vs. consumer software) and the specific sector13 in which the software is used (e.g. healthcare software).14
(15) In relation to functionality, in previous cases, the Commission classified software products into: (i) infrastructure software; (ii) middleware (i.e. integration platforms); (iii) application software and office software; and (iv) operating/browser software.15
(16) Within infrastructure software, the Commission has considered the following additional sub-segmentation: (i) security software; (ii) ITOM software; (iii) application development software; and (iv) storage management software.16
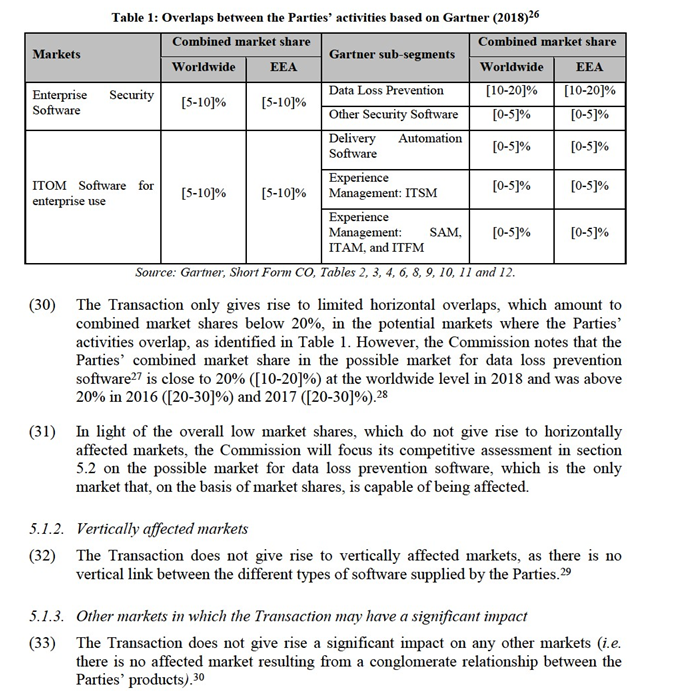
(17) Enterprise security software seeks to reduce the risk of unauthorised access to the data and IT systems of organisations. It is designed to improve the security of enterprise network infrastructures through security management, access control, authentication, encryption, data loss prevention, intrusion detection and prevention, vulnerability assessment, and perimeter defence, among others.17
(18) The overall enterprise security software category is divided by Gartner into the following nine sub-segments: (i) application security testing (dynamic and static); (ii) data loss prevention; (iii) enterprise endpoint protection; (iv) identity governance and administration; (v) secure e-mail gateways; (vi) secure web gateways;(vii) security information and event management; (viii) (web) access management; and (ix) other security software.18
(19) ITOM software for enterprise use monitors and controls the manner a company’s IT department approaches IT services, deployment, and support to ensure consistency, reliability, and quality. It represents all tools necessary to manage the provisioning, capacity, performance, and availability of the computing, networking and application environment.19
(20) Gartner delineates the overall ITOM software segment into the following sub- segments: (i) delivery automation, which is further subdivided into (a) general and (b) application release orchestration; (ii) experience management, which is further subdivided into (a) IT Services Management (“ITSM”) and (b) software asset management (“SAM”), IT asset management (“ITAM”), and IT Financial Management (“ITFM”); (iii) performance analysis, which is further subdivided into (a) artificial intelligence for operations, IT infrastructure monitoring and other monitoring tools, (b) application performance management, and (c) network performance monitoring and diagnosis; and (iv) other ITOM software not specifically covered within the above-named categories, including (a) ITOM mainframe tools and (b) other ITOM.
(21) Application development (“AD”) software for enterprise use includes tools that represent each phase of the software development life cycle (including planning, creating and verification). Within this category, Gartner’s sub-segmentation for AD mainframe tools covers specialised AD tools used to develop and maintain applications that run on mainframe computers.20
(22) The Commission has not examined AD mainframe tools in prior decisions, but it has reviewed the broader category of AD software and considered whether different types of AD software constitute separate product markets, ultimately leaving the exact market definition open.21 In line with Gartner’s segmentation, a possible product market for AD mainframe tools can be identified.
(23) The Notifying Party agrees with the Commission precedents that differentiate between software according to functionality and end-user. Consequently, the Notifying Party considers that the relevant product markets for the purpose of the Transaction are security software, ITOM software and AD software for enterprise use.22
(24) The Commission has not identified any reasons in this case to deviate from its precedents in which it defines the software industry market by reference to functionality and end-users as well as identifies the narrowest possible product markets. Among existing market intelligence reports which have been provided by the Notifying Party and have been used by the Commission in prior decisions, Gartner provides the most granular segmentations and will therefore be used in this decision. The potential markets for security software, ITOM software and AD software for enterprise end use may thus be further segmented on that basis, as described in paragraphs (18) to (21). Finally, the market investigation did not suggest alternative product market definitions.
(25) The Commission considers that, in any event, for the purposes of this decision, the exact product market definition with regard to the supply of infrastructure software can be left open, as the Transaction does not raise serious doubts as to its compatibility with the internal market or the functioning of the EEA Agreement under the narrowest possible product market definition, for which market share data is available, based on the Gartner segmentation.
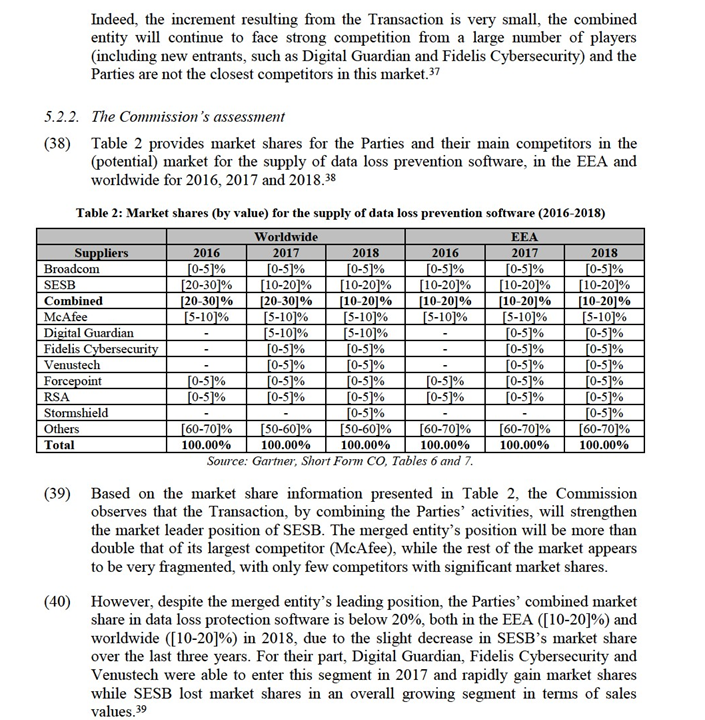
4.2.2. Geographic market definition
(26) In previous cases, the Commission concluded that the geographic market for infrastructure software (as well as any potential segmentations of that market) was worldwide or at least EEA-wide in scope, since customers consider offers from vendors from all parts of the world, there are no technological barriers that restrict vendors from supplying customers globally, and infrastructure software are broadly identical across different countries.23
(27) The Notifying Party agrees with the Commission’s precedents defining a worldwide market, arguing that, from a supply-side perspective, suppliers participate in projects regardless of the project’s location. In particular, by removing the physical presence of the software in a company premises, it is possible to supply companies located across the world through cloud computing. From a demand-side perspective, the Notifying Party submits that companies compare the effectiveness of different global manufacturers and source their infrastructure software products globally.24 Nevertheless, the Notifying Party also provided EEA-wide market shares.
(28) In any event, for the purposes of this decision, the exact geographic market definition with regard to the supply of infrastructure software (as well as any potential segmentations of that market) can be left open, as the Transaction does not raise serious doubts as to its compatibility with the internal market or the functioning of the EEA Agreement under any plausible geographic market definition.
5. COMPETITIVE ASSESSMENT
5.1. Affected markets
5.1.1. Horizontally affected markets
(29) As stated above, the Parties’ product portfolios only overlap with regard to the possible markets for enterprise security software and ITOM software for enterprise use and certain potential segmentations of that market. In line with the approach set out in paragraph (25), the narrowest possible markets in this regard correspond to the sub-segmentations provided by Gartner.25
(34) Broadcom has a market share above 30% in two Gartner sub-segments: (i) ITOM mainframe tools,31 where Broadcom has a [20-30]% market share in the EEA and [30-40]% worldwide and (ii) AD mainframe tools,32 where Broadcom has a [30- 40]% market share in the EEA and [40-50]% worldwide.33
(35) However, neither ITOM mainframe tools nor AD mainframe tools are closely related to SESB’s activities.34 First, the Parties indicate that SESB software products cannot be used on mainframe computer systems where Broadcom’s ITOM mainframe tools and its AD mainframe tools are used. Second, even if there are customers that purchase both Broadcom’s and SESB’s products, these purchases are intended for different purposes, as Broadcom’s products are used for mainframe computers and SESB’s products are used for other types of systems within the company or the company’s network as a whole. Accordingly, such customers do not qualify as common customers for the “same end use”, within the meaning of paragraph 91 of the Non-Horizontal Merger Guidelines. Third, even for overlapping customers, the two sets of products are not susceptible to bundling or tying practices, given that the products are not sold together to the same division within a customer organisation, or on the same timetables. While respondents to the market investigation mentioned Broadcom’s general tendency to employ bundling or tying strategies, no concerns were voiced as regards a possible bundling of Broadcom’s ITOM mainframe tools and/or AD mainframe tools with SESB’s software solutions. Moreover, all respondents confirmed that there are sufficient credible alternative suppliers to Broadcom in these two market segments. Likewise, all respondents, including competing suppliers of enterprise security software, indicated that they do not require access to Broadcom’s ITOM mainframe tools and/or AD mainframe tools in order to ensure interoperability.35
(36) This general view conforms to Broadcom’s internal documents assessing the Transaction, which do not envisage Broadcom’s ITOM mainframe tools or its AD mainframe tools or any conglomerate strategy in relation to these products.36
5.2. Horizontal non-coordinated effects
5.2.1. The Notifying Party’s view
(37) According to the Notifying Party, the Transaction will not raise any competition concerns in the (potential) market for the supply of data loss prevention software.
(41) The Commission also notes that the Transaction will not have a significant effect on the market structure in the EEA or worldwide for the supply of data loss prevention software. As shown in Table 2, the market share increment brought about by the Transaction is very limited (below [0-5]% worldwide and in the EEA throughout the last three years).
(42) Furthermore, there is a large number of alternative suppliers of data loss prevention software active both worldwide and in the EEA. All of these suppliers, including McAfee, Digital Guardian, Fidelis Cybersecurity and Venustech, as well as Forcepoint and RSA, will continue to compete effectively with the merged entity post-Transaction.
(43) Finally, the evidence on file suggests that the Parties are not particularly close competitors in this market. While SESB is the market leader, Broadcom is a small player on this market and its “CA Data Protection” product is a legacy solution, […].40 Therefore, Broadcom currently does not seem to constitute an important competitive constraint in this market.
(44) Further, the Commission notes that similar arguments equally apply to the potentially broader market for enterprise security software. In any event, the Parties’ combined market share for 2018 was [5-10]% worldwide and [5-10]% in the EEA, which is well below 20%.
5.2.2.1. Conclusion
(45) In light of the foregoing, the Commission concludes that the Transaction does not raise serious doubts as to its compatibility with the internal market or the functioning of the EEA Agreement in the (potential) market for the supply of data loss prevention software or the broader market for enterprise security software, in the EEA or worldwide.
6. CONCLUSION
(46) For the above reasons, the European Commission has decided not to oppose the notified operation and to declare it compatible with the internal market and with the EEA Agreement. This decision is adopted in application of Article 6(1)(b) of the Merger Regulation and Article 57 of the EEA Agreement.
1. OJ L 24, 29.1.2004, p. 1 (the “Merger Regulation”). With effect from 1 December 2009, the Treaty on the Functioning of the European Union (the “TFEU”) has introduced certain changes, such as the replacement of “Community” by “Union” and “common market” by “internal market”. The terminology of the TFEU will be used throughout this decision.
2. OJ L 1, 3.1.1994, p. 3 (the “EEA Agreement”).
3. Publication in the Official Journal of the European Union No C 333, 4.10.2019, p. 18.
4. Endpoints are remote computing devices, such as laptops, tablets or smart phones, that connect to a network and communicate with the network. Short Form CO, footnote 21.
5. The Transaction does not include Symantec’s LifeLock ID Analytics business unit (providing identity theft protection solutions), which is currently reported as part of the enterprise security segment. Short Form CO, paragraphs 6 and 32.
6. Short Form CO, Annex 3.1.1 (Asset Purchase Agreement).
7. Turnover calculated in accordance with Article 5 of the Merger Regulation.
8. See, for instance, Commission decision of 8 March 2017 in case M.8223 – Micro Focus/HPE Software Business.
9. The market intelligence company IDC also provides market data and analysis about the information technology sector and has also been used by the Commission in previous decisions. See, for instance, Commission decision of 26 January 2011 in case M.5984 – Intel/McAfee. However, for the purpose of the present decision, Gartner’s segmentation provides the most granular segmentations. For instance, for the enterprise security software segment, Gartner provides nine sub-segments while IDC lists only seven sub- segments for security software and does not provide separate data for enterprise security software solutions. Based on the IDC segmentation, there are no affected possible markets resulting from the Transaction.
10. In the course of the market investigation, the software supplier Trend Micro mentioned the existence of a commercial agreement that it has with Broadcom that enables Broadcom to run certain Trend Micro software on certain of its semiconductors. This agreement concerns Broadcom’s application-specific standard products (“ASSPs”) with on-chip processors (i.e. systems-on-a-chip (“SoCs”)) used in consumer devices such as residential gateway units (e.g. cable modems, DSL gateways, consumer routers) or set-top boxes. Broadcom’s SoCs used in the central processing units of these devices may contain Trend Micro’s consumer software products. This commercial agreement relates to non-enterprise security software (i.e. consumer security software that runs on consumer devices), a separate product market based on the end- use segmentation considered in paragraph (14), section 4.2.1 below. In any event, information provided by the Notifying Party shows that SESB’s software solutions do not run on Broadcom’s SoCs such that they cannot be considered “closely related” to Broadcom’s SoC products within the meaning of paragraph 91 (relating to possible conglomerate effects) of the Commission’s Non-Horizontal Merger Guidelines (Guidelines on the assessment of non-horizontal mergers under the Council Regulation on the control of concentrations between undertakings, OJ C 265, 18.10.2008). As it is technically not possible to combine the two products, they cannot be considered to be complementary products that are generally purchased by the same set of customers for the same end use. Consequently, Trend Micro’s agreement with Broadcom will not be impacted by the Transaction. Similarly, application-specific integrated circuits (“ASICs”) – the main semiconductor type sold by Broadcom – are not “closely related” to SESB’s software. ASICs are used for analogue processing or adjacent tasks. Given their application-specific nature, ASICs are not able to run any general-purpose software such as enterprise security software. Notifying Party’s reply of 13 October 2019 to RFI 3, question 1.
11. In the course of the market investigation, the software supplier McAfee indicated that it relies on Broadcom’s ASSPs used in IP/Ethernet switches/routers (in particular Broadcom’s StrataXGS product line as well as Broadcom’s corresponding software development kit (“SDK”) suite) for McAfee’s network security platform (“NSP”) product offering. While McAfee stressed the importance of ensuring interoperability going forward, McAfee did not observe any merger-specific impact resulting from the Transaction (Reply of McAfee to questionnaire Q1 to competitors and customers, questions 7.1 and 8.1; McAfee’s email response of 16 October 2019). Indeed, the Notifying Party confirms that McAfee’s NSP does not compete with any SESB products and belongs to Gartner’s overall data center systems market segment and that it is technically impossible to integrate such software directly in IP/Ethernet switches/routers as they run at different layers of the OSI Model (i.e. the reference model for how applications communicate over a network, breaking down data transmission into seven layers). Notifying Party’s reply of 13 October 2019 to RFI 3, question 8; Notifying Party’s reply of 22 October 2019 to RFI 6, question 1. Therefore, there is also no theoretical vertical relationship between SESB and Broadcom’s activities in the supply of ASSPs used in IP/Ethernet switches/routers. In any event, according to the Notifying Party, there is no potential for a degradation of interoperability. Broadcom’s SDK suite is provided to all customers purchasing Broadcom’s devices and any degradation of the SDK provided to Broadcom’s customers would impair the ability of the IP/Ethernet switch/router to operate for any purpose (not simply with respect to McAfee’s NSP product). Notifying Party’s reply of 13 October 2019 to RFI 3, questions 7-9. The merged entity will therefore have no ability or incentive to deteriorate or stop providing access to interoperability information to McAfee.
12. Commission decision of 29 April 2008 in case M.5080 – Oracle/Bea, paragraph 8 and Commission decision of 8 March 2017 in case M.8223 – Micro Focus/HPE Software Business, paragraph 16.
13. The segmentation by sector in which the software is used is not relevant in the context of the Transaction. Both Parties supply their enterprise software to a wide range of sectors and do not focus on sector-specific software solutions (Short Form CO, Annexes 5.3.25 and 5.3.26). Therefore, the Commission will not discuss further a potential segmentation by sector for the purpose of the present decision.
14. Commission decision of 20 June 2011 in case M.6237 – Computer Sciences Corporation/iSoft Group, paragraphs 22-25 and Commission decision of 8 March 2017 in case M.8223 – Micro Focus/HPE Software Business, paragraph 17.
15. Commission decision of 20 June 2011 in case M.6237 – Computer Sciences Corporation/iSoft Group, paragraph 23; Commission decision of 15 December 2014 in case M.7458 – IBM/INF Business of Deutsche Lufthansa, paragraph 35; and Commission decision of 8 March 2017 in case M.8223 – Micro Focus/HPE Software Business, paragraph 18.
16. Commission decision of 8 March 2017 in case M.8223 – Micro Focus/HPE Software Business, paragraph 19.
17. Short Form CO, paragraph 46.
18. Consumer security software solutions are not part of Gartner’s enterprise security software segment. Short Form CO, paragraph 43, footnote 19.
19. Short Form CO, paragraph 48.
20. Mainframe computers differ from standard PCs in several ways such as using different processor instruction sets. Notifying Party’s reply of 22 October 2019 to RFI 5, question 1.
21. Commission decision of 8 March 2017 in case M.8223 – Micro Focus/HPE Software Business, paragraph 32; Commission decision of 5 March 2008 in case M.4747 – IBM/Telelogic, paragraph 122; Commission decision of 20 February 2003 in case M.3062 – IBM/Rational, paragraphs 11, 16, 20, and 23.
22. Short Form CO, paragraphs 51-52; Notifying Party’s reply of 22 October 2019 to RFI 5, question 1.
23. Commission decision of 29 April 2008 in case M.5080 – Oracle/Bea, paragraphs 14-15; Commission decision of 21 October 2010 in case M.5529 – Oracle/Sun Microsystems, paragraphs 767-769 and Commission decision of 8 March 2017 in case M.8223 – Micro Focus/HPE Software Business, paragraph 36.
24. Short Form CO, paragraph 55.
25. Based on the IDC segmentation, the Parties overlap in the following security software sub-segments: (i) identity and digital trust software, (ii) endpoint security software, and (iii) security analytics, intelligence, response, and orchestration. None of these sub-segments are affected as a result of the Transaction. Short Form CO, Annex 6.1.1.
26. The market share provided by the Parties is based on Gartner information. The market share estimates provided for the EEA includes EEA Member States and Gartner's "Other Eastern Europe" and 'Other Western Europe" categories (including Albania, Andorra, Bosnia & Herzegovina, Croatia, Cyprus, Estonia, Faroe Islands, Gibraltar, Greenland, Guernsey, Isle of Man, Iceland, Jersey, Latvia, Liechtenstein, Lithuania, Luxembourg, Macedonia, Malta, Moldova, Monaco, Montenegro, San Marino, Slovakia, Slovenia and Svalbard). Excluding Gartner's "Other Eastern Europe" and "Other Western Europe" categories, the Parties combined market shares for 2018 in the EEA would remain at [5-10]% in Entreprise Security Software ([10-20]% in Data Loss Prevention, [0-5]% in Other Security Software) and [5-10]% in ITOM Software ([0-5]% in Delivery Automation Software, [0-5]% in Experience Management: ITSM, [0-5]% in Experience Management : SAM, ITAM and ITFM).
27. Short Form CO, paragraph 47.
28. Short Form CO, Tables 6 and 7.
29. As explained in footnote 11, there is no vertical relationship either between SESB and Broadcom's activities in the supply of certain semiconductor products (i.e. ASSPs for IP/ Ethernet switches / routers).
30. As explained in footnote 10, there is no conglomerate relationship either between SESB and Broadcom’s activities in the supply of certain semiconductor products (i.e. ASSPs for residential gateway units and set-top boxes).
31. ITOM mainframe tools include tools for managing and monitoring mainframe implementations, including application performance monitoring, monitoring, database management, systems management, automation, workload automation and IT process automation. Short Form CO, paragraph 44, footnote 31.
32. AD mainframe tools include tools that represent each phase of the software development life cycle (including planning, creating and verification). AD mainframe tools are specialised AD tools used to develop and maintain applications that run on mainframe computers, which differ from standard PCs in several ways (such as using different processor instruction sets). Notifying Party’s reply of 22 October 2019 to RFI 5, question 1.
33. Short Form CO, paragraphs 109-110.
34. Short Form CO, paragraphs 109-111.
35. Replies to questionnaire Q1 to competitors and customers, questions 3-5 and 9-11.
36. Short Form CO, Annexes 5.3.1-5.3.24.
37. Short Form CO, Paragraphs 66-73.
38. The market sahre provided by the Parties is based on Gartner information. The 2016 and 2017 share estimates provided by the EEA include Member States and Gartner's "Other Eastern Europe" and "Other Western Europe" categories. If these categories had been added, the Parties' combined shares for 2018 in the EEA would be [10-20]%.
39. The same downward trend can be observed in the broader market for entreprise security software, in which the Parties' combined share decreased slighltly from [10-20]% to [5-10]% in the EEA between 2016 and 2018. Short Form CO, Tables 4 and 5.
40. Short Form CO, paragraph 73.